Cyber experts issue protection advice following NHS ransomware attack
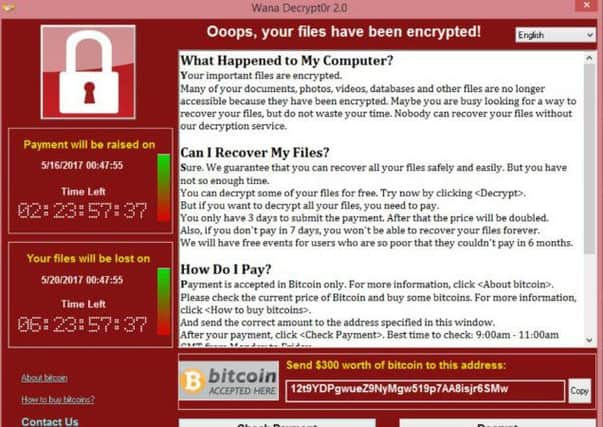

The ‘Wannacry’ ransomware has spread unchecked through unprotected systems, including many NHS networks in the UK running the outdated Windows XP operating system, which has been unsupported since 2014.
The Crown Commercial Service paid Microsoft £5.5m for one year’s extra support to give government departments 12 months to upgrade their systems, but the additional cost of upgrading the proprietary software meant that many computers were left running the vulnerable XP system.
Advertisement
Hide AdAdvertisement
Hide AdFollowing the spread of the virus globally, Microsoft has since issued an “highly unusual” emergency update.
However, it has been reported that new strains of the virus, possibly created after the discovery of the ‘kill switch’ for the existing Wannacry and Microsoft’s update, could start to spread in a similar pattern.
It is with this in mind that the National Crime Agency (NCA), which is working closely with a range of partners both in the UK and overseas, has issued the following advice:
Key Protect messages for businesses to protect themselves from ransomware:
Advertisement
Hide AdAdvertisement
Hide Ad- Install system and application updates on all devices as soon as they become available.
- Install anti-virus software on all devices and keep it updated.
- Create regular backups of your important files to a device that isn’t left connected to your network as any malware infection could spread to that too.
Additionally, for individual users:
- Only install apps from official app stores, such as Google’s Play Store, or Apple’s App Store as they offer better levels of protection than some third party stores. Jailbreaking, rooting, or disabling any of the default security features of your device will make it more susceptible to malware infections.
Advertisement
Hide AdAdvertisement
Hide AdThe National Cyber Security Centre’s latest technical guidance includes specific software patches to use that will prevent uninfected computers on your network from becoming infected with the “WannaCry” ransomware: https://www.ncsc.gov.uk/guidance/ransomware-latest-ncsc-guidance
Additional in-depth technical guidance on how to protect your organisation from ransomware is also available from the NCSC at https://www.ncsc.gov.uk/guidance/protecting-your-organisation-ransomware and on the Microsoft website: http://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=Ransom:Win32/WannaCrypt.
Although Wannacry has been able to spread across networks without any user intervention, there will always be a point where one user in an organisation has clicked on an email link or somehow inadvertently kicked off the journey of the virus across their network. The NCSA has therefore reiterated its usual advice on cyber security:
“Criminals use opportunities like this to further defraud people using phishing and smishing tactics. We would therefore urge people to be cautious and wary when contacted by people who claim to be from the NHS in relation to the ransomware attack.”
Advertisement
Hide AdAdvertisement
Hide AdTheir advice for protection against phishing and smishing (SMS phishing, via text) is as follows:
●- An email address can be spoofed. Don’t open attachments or click on the links within any unsolicited emails you receive, and never respond to emails that ask for your personal or financial details.
●- The sender’s name and number in a text message can be spoofed, so even if the message appears to be from an organisation you know of, you should still exercise caution; particularly if the texts are asking you to click on a link or call a number.
- Don’t disclose your personal or financial details during a cold call, and remember that the police and banks will never ring you and ask you to verify your PIN, withdraw your cash, or to transfer your money to another “safe” account.
Advertisement
Hide AdAdvertisement
Hide AdAny individuals or businesses who believe they have been a victim of the ransomware attack are urged to report to Action Fraud.
For up to date fraud and cyber crime alerts, people are advised to visit the Action Fraud website and follow us on Twitter and Facebook.